Understanding Virus Analysis: Execution, System Hijacking, and Manual Analysis Techniques

Introduction to Virus Analysis
Virus analysis, often referred to as malware analysis, is the process of examining malicious software to understand its behavior, purpose, and potential impact on systems. This field is crucial in cybersecurity for identifying threats, developing defenses, and mitigating attacks. Malware encompasses various types, including viruses, worms, Trojans, ransomware, and spyware, each designed to exploit vulnerabilities in computer systems.
The primary stages of malware analysis include static analysis, where the code is examined without execution; dynamic analysis, involving running the malware in a controlled environment to observe its actions; behavioral analysis, focusing on interactions with the system; and reverse engineering, which involves disassembling the code to uncover its inner workings. Automated tools can scan for signatures or anomalies, while manual methods provide deeper insights.

The goal is to determine how the malware infects, persists, and exfiltrates data, enabling security professionals—and even informed users—to protect against similar threats. For everyday users, understanding basic analysis can help in spotting suspicious files before they cause harm.
How Malware Executes and Hijacks Systems (Focus on Windows)
Malware execution begins with infection vectors, where the malicious file enters the system. Common entry points include phishing emails with attachments, drive-by downloads from compromised websites, infected removable drives like USBs, or exploitation of software vulnerabilities. Once inside, the malware must execute to perform its payload.
Execution Mechanisms
On Windows systems, malware often masquerades as legitimate files, such as executables (.exe), scripts (.vbs, .ps1), or documents with macros (.docm). Execution can occur through:
- User Interaction: Double-clicking an infected file or enabling macros in Office documents triggers the code.
- Auto-Run Features: Malware exploits Windows features like AutoRun on USB drives or scheduled tasks to launch automatically.
- Exploits: Zero-day vulnerabilities in software (e.g., Adobe Flash or browsers) allow silent execution without user input.
- Fileless Malware: This resides in memory, using legitimate tools like PowerShell to run scripts without writing files to disk, making detection harder.
Upon execution, malware unpacks itself if obfuscated, allocates memory, and begins its operations. For instance, ransomware encrypts files and demands payment, while spyware logs keystrokes or steals data.
System Hijacking Techniques
Hijacking involves gaining control over system resources for persistence, evasion, and propagation. Windows is particularly targeted due to its widespread use and complex architecture. Key techniques include:

Typical steps of ransomware life cycle.
Hijacking involves gaining control over system resources for persistence, evasion, and propagation. Windows is particularly targeted due to its widespread use and complex architecture. Key techniques include:
- Registry Modifications: Malware alters the Windows Registry (e.g., HKLM\Software\Microsoft\Windows\CurrentVersion\Run) to auto-start on boot. This ensures persistence across reboots.
- DLL Hijacking: Attackers place malicious DLLs in directories searched by applications, exploiting the DLL search order. When a program loads a DLL, the fake one executes instead, injecting code into legitimate processes.
- Process Injection: Malware injects code into running processes like explorer.exe or svchost.exe to hide its activity and gain elevated privileges.
- Scheduled Tasks: Using schtasks.exe, malware creates tasks to run periodically, often for reinfection or command-and-control (C2) communication.
- Shortcut (LNK) Exploitation: Malicious LNK files mimic innocent shortcuts but execute payloads when clicked.
- Rootkits: Advanced malware hides in the kernel, intercepting system calls to conceal files, processes, or network activity.
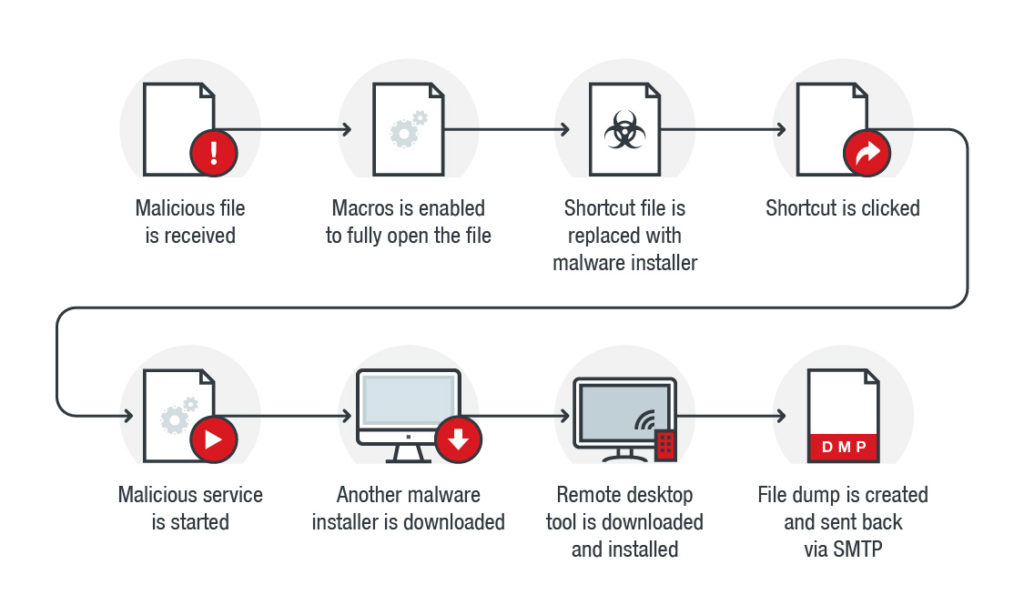
Malicious macro infection chain showing shortcut hijacking.
These methods allow malware to steal data, encrypt files (as in ransomware), or turn the system into a botnet node. For example, in DLL hijacking, the search order starts from the application's directory, moving to system folders, allowing attackers to drop malicious DLLs in vulnerable paths.
Once hijacked, the system may exhibit symptoms like slowed performance, unexpected pop-ups, or unauthorized network traffic. Prevention involves keeping Windows updated, avoiding suspicious downloads, and using security software.
Reverse Engineering: Manual File Analysis for Connections by Normal Users
Reverse engineering (RE) involves deconstructing malware to understand its code, logic, and capabilities. While advanced RE requires expertise, normal users can perform basic manual analysis to inspect a file's connections-such as network communications to C2 servers-using accessible tools. This helps verify if a file is malicious without deep coding knowledge.

A flow chart of reverse engineering process.
Basic Concepts of Reverse Engineering
RE starts with static analysis (examining the file without running it) and progresses to dynamic analysis (observing runtime behavior). For connections, focus on identifying IP addresses, domains, or API calls related to networking. Tools like disassemblers reveal code, while monitors track interactions.
Step-by-Step Manual Analysis for Connections
-
Initial Triage (Static Analysis):
- Use free tools like Strings (from Sysinternals) to extract readable text from the file. Look for URLs, IPs, or strings like "http://" or "connect()".
- Check file properties with PEiD or Exeinfo PE to identify packers/obfuscators.
- Upload to VirusTotal for automated scans, which often reveal known C2 domains.
-
Disassembly (Deeper Static RE):
- Download Ghidra (free from NSA) or IDA Freeware. Load the file and search for network-related functions (e.g., Winsock APIs like socket(), connect(), send()).
- Look for hardcoded IPs or domains in the code. For beginners, tutorials on Ghidra can guide navigation.
-
Dynamic Analysis in a Safe Environment:
- Use a virtual machine (VM) like VirtualBox to isolate the file. Run the suspicious file inside.
- Monitor network traffic with Wireshark: Capture packets to see outgoing connections. Filter for HTTP/HTTPS or unusual ports.
- Use TCPView (Sysinternals) to view real-time connections, noting any suspicious IPs.
- Process Explorer can show process trees and loaded DLLs, helping spot injected code making connections.
-
Behavioral Observation:
- Run ProcMon (Process Monitor) to log file, registry, and network activity. Filter for network events to trace connections.
- If the file attempts to phone home, block it and analyze the destination IP via WHOIS or threat intelligence sites.
Reverse Engineering Process Flowchart.
Caution: Always perform analysis in a sandboxed environment to avoid infecting your main system. Resources like "Practical Malware Analysis" book or online workshops provide beginner-friendly guidance. This manual approach empowers users to detect connections indicative of spyware or botnets, potentially preventing data exfiltration.
Recommended Antivirus Tools
While manual analysis is valuable, antivirus software provides automated protection. Based on 2025 reviews, here are some top options evaluated for detection rates, features, and usability:
| Antivirus | Key Features | Pros | Cons | Price (2025 Estimate) |
|---|---|---|---|---|
| Bitdefender Antivirus Plus | Real-time scanning, ransomware protection, VPN. High detection rates. | Excellent malware blocking; low system impact. | Limited free version. | Starts at $30/year. |
| Norton 360 | Comprehensive suite with firewall, password manager, dark web monitoring. | Strong against phishing; family plans available. | Can be resource-heavy. | From $50/year. |
| ESET NOD32 | Lightweight, advanced heuristics for unknown threats. | Fast scans; good for gamers. | Fewer extras than competitors. | Around $40/year. |
| Malwarebytes | Focus on malware removal, adware blocking. Free version for on-demand scans. | Effective against PUPs; easy to use. | Premium needed for real-time protection. | Premium from $45/year. |
| Windows Defender (Built-in) | Integrated with Windows; real-time protection, cloud-based detection. | Free; no installation needed. | May miss some advanced threats. | Free with Windows. |
Choose based on needs-Bitdefender for top-tier protection, or Windows Defender for simplicity. Always combine with safe browsing habits for best results.
